Did you know that as many as 65% of employees engage in risky behaviors on company devices? Such actions can directly expose your organization to numerous cyber threats, including phishing and ransomware, which primarily aim to compromise your company’s data.
To effectively counter constantly evolving threats, companies should implement advanced strategies and best practices for data protection, including the Zero Trust approach. But what does this mean in practice, and what role does a password manager play in this concept?
What Is the Zero Trust Strategy?
The Zero Trust strategy is based on a simple yet fundamental principle: „Never trust, always verify.” This means that every attempt to access resources—whether by users or devices—must be authorized, regardless of whether it occurs within or outside the corporate network. In practice, this requires:
- Continuous verification: A requirement for constant authorization, regardless of previous actions or user permissions.
- Minimization of trust: Users should only have access to the data and systems that are essential for their work.
- Dynamic control: Real-time monitoring of activities to quickly detect and respond to anomalies or suspicious behavior.
Why Is Zero Trust Strategy So Important?
Traditional security approaches that rely on securing corporate networks with firewalls are simply no longer sufficient. With remote and hybrid work models and rapidly evolving cyber threats, companies need solutions that not only help prevent incidents but also significantly limit the spread of potential breaches.
Unfortunately, fully trusting internal users is a recipe for disaster.
However, Zero Trust does not mean treating employees with suspicion—it is a strategy that aligns access levels with actual needs and eliminates security gaps.
How Does a Password Manager Fit into the Zero Trust Strategy?
Modern password managers are more than just tools for storing login credentials—they are the foundation of effective access management and cybersecurity resilience. Their features align seamlessly with the Zero Trust framework, offering organizations:
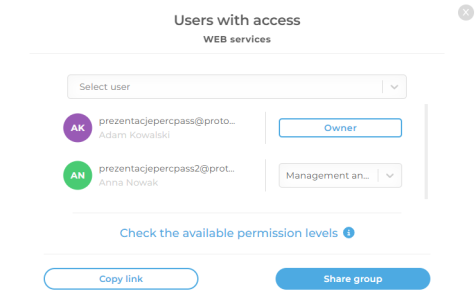
Precise Access Management
Through the creation of access groups and controlled data sharing, administrators can assign access to specific resources only to users who truly need them for their work.
Multi-Factor Authentication (MFA)
A password alone is no longer enough. In today’s cybersecurity landscape, using at least two-factor authentication (2FA) is essential, which includes:
- Something you know – A password
- Something you have – A code from an authentication app
- Something you are – Biometric verification
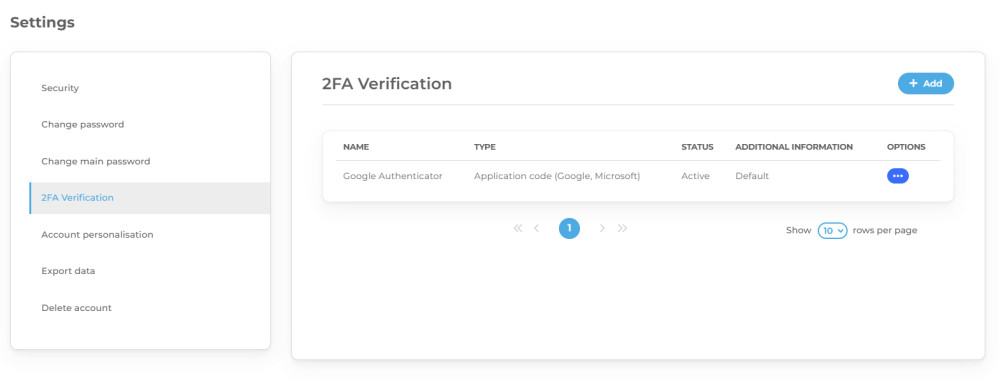
Stealing a password alone does not grant automatic access to data, making MFA a critical security measure that should be a standard practice.
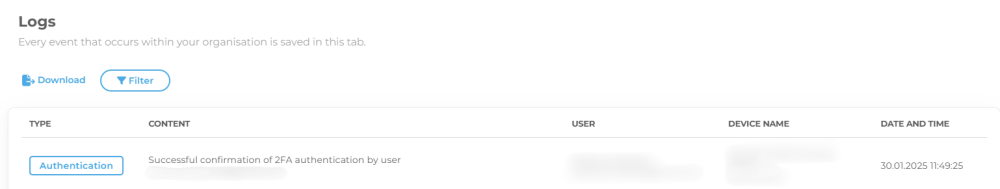
Activity Monitoring
Implemented monitoring and reporting features allow organizations to collect system logs, providing clear records of who performed what actions on stored credentials. These logs help detect and address security incidents that could threaten the organization. Additionally, all logins to perc.pass are archived, ensuring that any unauthorized access attempts immediately raise red flags.
Use a Password Manager That Supports Zero Trust
Corporate data, including confidential information, client data, and proprietary knowledge, is among the most valuable assets of any organization. In today’s cybersecurity landscape, implementing a Zero Trust strategy supported by modern password managers is not a luxury—it is a necessity.
Don’t take risks—ensure your company’s security. By investing in the right tools and employee education, you can significantly reduce the risk of data breaches, improve regulatory compliance, and build a strong foundation for cyber resilience.
Want to learn more about perc.pass, the first Polish password manager? Check out our Security Whitepaper or contact us today.



